A recent FBI warning about “juice jacking” has drawn lots of media attention—but there is no indication of any legitimate reason to worry.
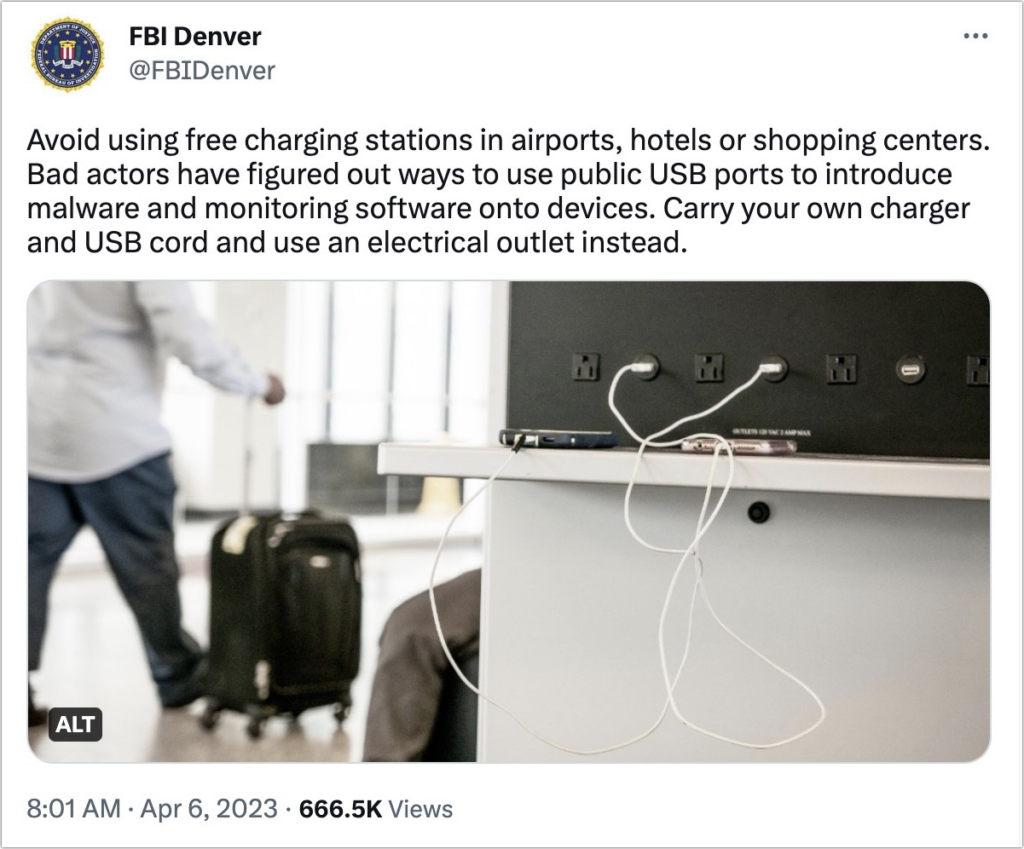
“Juice jacking” is the theoretical act of installing malware on, or stealing data from, an iPhone connected to a public charging station. Researchers first demonstrated “juice jacking” at the 2011 Defcon security conference.
Concerning its tweet, the Denver office of the FBI said it was simply a standard public-service announcement. And one of the original researchers on “juice jacking” was quoted as saying that he is not aware of a “juice jacking” kiosk existing in a public place outside of a security conference.
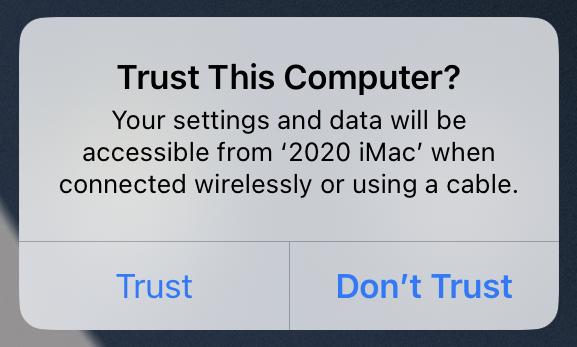
Additionally, Apple has made security changes to iOS and iPadOS, making the risk of “juice jacking” even less concerning. Now, when you connect a device to a USB charger or device that does anything beyond providing power, you will see a prompt asking if you trust it. While it is highly improbable that you will get such a prompt when connecting to a public charging station, if it does occur, tap “Don’t Trust” and unplug your device immediately.
Additional measures you could take to block all possibility of juice jacking include:
- Bring your own USB charger and plug it into a standard wall outlet.
- Charge your iPhone from a battery pack and recharge the battery from a public charger.
- Use a public wireless Qi charger.
- Connect a USB data blocker to the end of your charging cable when using a public charger.
- Rely on a special USB cable that can only charge, not carry data.
But remember: the latest warnings in the news about “juice jacking” do not seem to be based on any documented instances. It is sensible to bring a USB charger while traveling and carry a battery pack as a backup—but there is no reason to worry about security when using a public charger.